Entropy: Pyth Network's Solution for Secure On-Chain Randomness
The need for secure and reliable random number generation on blockchain networks.
Table of Contents:
1. INTRODUCTION
Blockchain applications, from NFT mints to decentralized gaming, often rely on random number generation, but achieving true on-chain randomness has been a persistent challenge. (i) The deterministic nature of blockchains, (ii) vulnerability to manipulation by miners or validators, (iii) slow response times, (iv) and lack of trust in randomness sources have all hindered progress.
These limitations pose significant obstacles to fairness and security in decentralized applications, potentially stifling innovation and user adoption. As the DeFi and Web3 spaces continue to evolve, overcoming these hurdles in random number generation has become increasingly critical for building trustworthy, efficient, and engaging blockchain-based platforms that can rival their centralized counterparts.
2. Limitations of On-Chain Randomness
The term “randomness” refers to the lack of pattern or predictability. The outcome of a coin toss, the pattern of a fingerprint, and the shape of a snowflake are all considered to be unpredictable. While unpredictable outcomes are abundant in nature, the same can’t be said for randomness generated by computers. As computers are deterministic devices, it may not be possible to generate truly random numbers purely through a set of computer algorithms [2].
2.1 Deterministic Nature of Blockchains:
Blockchain systems are inherently deterministic. Every node in the network must be able to independently verify the same outcomes given the same inputs, making it difficult to introduce true randomness without external input [1].
Meaning they operate in a predictable way based on predefined rules and code. This clashes with the concept of true randomness, which is inherently unpredictable.
2.2 Vulnerability to Manipulation:
“Miners” or “validators” can potentially influence the outcome of a random number generation by withholding or reordering transactions, compromising the fairness and security of the process.
2.2.1 proof-of-work
In proof-of-work blockchains, “miners” have the power to decide which transactions to include in a block, and they can even decide to delay or omit blocks altogether.
2.2.2 Proof-of-Stake
In proof-of-stake systems, “validators” have a similar influence over block production. This power can be used to cherry-pick data that leads to favorable results in applications that rely on randomness.
Example: Imagine an on-chain gambling game that uses block hashes to determine the outcome of a bet. A miner with a stake in the game could potentially manipulate the block hash to ensure they win the bet, undermining the fairness of the game.
2.3 Slow Response Times:
Generating and verifying random numbers on-chain can be time-consuming, leading to slow response times that negatively affect the user experience, especially in real-time applications like gaming.
The speed of block generation varies across different blockchains. Bitcoin, for example, has an average block time of 10 minutes [3], while Ethereum aims for around 12 seconds [4]. In applications where randomness is needed quickly, such as fast-paced online games, these delays can be detrimental to the user experience.
2.4 Lack of Trust in the Randomness Source:
Users and developers must have confidence that the source of randomness is truly random and free from manipulation. A lack of trust in the randomness source can undermine the fairness and integrity of the application.
Moreover, some blockchains rely on internal sources of randomness, such as block hashes or transaction data, which may not be sufficient for high-security applications. Others use external oracles to provide randomness, but the reliability and trustworthiness of these oracles may be questioned.
Example: In a decentralized finance (DeFi) application that uses randomness to distribute rewards or airdrops, users need to trust that the randomness generation process is fair and unbiased. If there are doubts about the randomness source, it can undermine the credibility of the entire application.
3. Pyth Network's Entropy
Pyth Entropy is an innovative approach for delivering secure random numbers on the blockchain and has launched on mainnet. Entropy is a response to the community’s demand for a fast and cheap source of on-chain randomness [5].
The term “entropy” refers to a scientific concept that is most commonly associated with a state of disorder, randomness, or uncertainty. The term and the concept are used in diverse fields, from classical thermodynamics, where it was first recognized, to the microscopic description of nature in statistical physics, and to the principles of information theory [10].
3.1 Rapid Response Time:
Entropy ensures quick generation and verification of random numbers, significantly improving the user experience for time-sensitive applications.
Unlike traditional on-chain randomness methods that rely on block confirmations, Entropy leverages a "pull" model [6]. This means that users directly request random numbers from the Pyth network, eliminating the need to wait for block times. This results in near-instantaneous generation and verification of random values.
3.1.1 Push vs Pull Oracle
Push and pull oracles differ on a number of important dimensions:
Update frequency. In a “push oracle”, every price feed updates at a fixed update frequency. The oracle operator determines the frequency, but it typically ranges from every 10 minutes to 1 hour. In contrast, “pull oracles” on Pyth can update at a much higher frequency. For example, every Pyth price feed updates every “400 milliseconds”.
Latency. An oracle's update frequency also affects its prices' latency. The higher update frequencies of pull oracles allow applications to access lower-latency data.
Blockchain support. Pull oracles support a wide variety of different blockchains. Push oracles typically support a smaller number of blockchains, as each additional chain requires ongoing gas expenditures.
Price feed selection. Similar to the item above, pull oracles also support a wide selection of price feeds. In contrast, push oracles typically have a more limited selection. Push oracles generally cannot support a wide selection of feeds due to the gas cost of periodically updating each feed [6].
3.2 Strong Security Guarantees:
By leveraging advanced cryptographic techniques, Entropy ensures that the generated randomness is secure and resistant to manipulation, providing a high level of trust.
Moreover, entropy employs a robust commit-reveal scheme based on advanced cryptographic techniques. This involves multiple steps to ensure the randomness is unpredictable and resistant to tampering. First, a commitment to the random value is generated and publicly posted. Then, after a delay, the actual value is revealed. This separation of commitment and reveal phases ensures that the final random number cannot be manipulated.
3.3 Easy Integration:
Designed with developers in mind, Entropy offers straightforward integration, allowing for seamless adoption across various blockchain applications.
Pyth Entropy is designed with developer-friendliness in mind. It provides simple APIs and libraries for easy integration into smart contracts and dApps. This reduces the complexity of incorporating reliable randomness into various blockchain applications, saving developers time and effort [7].

3.4 Blockchain-Agnostic Design:
Entropy is designed to be compatible with multiple blockchain platforms, making it a versatile solution for the wider Web3 ecosystem.
Pyth Entropy is not limited to a single blockchain. It is built to be compatible with various blockchain platforms, including Ethereum, Solana, BNB Chain, and more. This flexibility enables developers to leverage Entropy's reliable randomness across a wide range of Web3 ecosystems and applications [8].
4. How Pyth Entropy Works
Pyth Entropy employs a “commit/reveal protocol” [11] optimized for on-chain usage, where a provider commits to a sequence of random numbers using a hash chain, and users can request and verify the random numbers to ensure that neither the provider nor the user can manipulate the outcome. This ensures the randomness is verifiable and secure as long as one of the parties remains honest."
4.2 Verifiable Delay Functions (VDFs):
VDFs introduce a delay in the generation of randomness, making it infeasible for any single party to manipulate the outcome within a short timeframe. This helps prevent front-running and other forms of manipulation.
Moreover, VDFs are a key component in the randomness generation process. VDFs require a specific amount of time to compute, ensuring that the output cannot be predicted or manipulated within a short timeframe. This feature makes it significantly more difficult for malicious actors to game the system [9].

4.3 External Entropy Sources:
By incorporating randomness from external, unpredictable sources (e.g., real-world events or hardware random number generators), Entropy enhances the unpredictability and security of the generated random numbers [10].
4.4 Cryptographic Proofs:
Pyth Entropy relies on cryptographic proofs to ensure the integrity and correctness of the randomness generation process. These proofs provide verifiable evidence that the random numbers were generated according to the protocol's rules and have not been tampered with. This transparency adds a crucial layer of trust and reliability to the system.[11]
4.4.1 Setup Phase:
Provider P computes a sequence of N random numbers:
Alice (Provider P in the statement) would generate a sequence of random numbers: x_{N-1}, x_{N-2}, ..., x_1, x_0.
Each x_i is derived from x_{i+1} using a hash function: x_i = hash(x_{i+1}).
The "Secret Key" in the diagram could represent x_{N-1}, the last number in this sequence.
4.4.2 Request Phase:
A user U (BOB) generates their own random number x_U and submits its “hash” h_U to the contract.
The contract assigns a sequence number i to this request.
The user requests the i'th random number from the provider off-chain.
The provider (Alice) reveals x_i to the user after verifying the sequence number.
The user submits both x_i and x_U to the contract.
The contract verifies the integrity of x_i and x_U using their respective hashes.
If verified, the final random number r is generated using both x_i and x_U.
4.4.3 This protocol ensures:
Randomness. As long as either the provider or user is honest, r is truly random.
Non-manipulation. Neither party can predict or manipulate the final random number.
Verifiability. The contract can verify the correctness of the revealed numbers.
Sequence integrity. The hash chain prevents the provider from changing past numbers.
5. Impact on DeFi and Web3
The introduction of Entropy could have far-reaching implications for the DeFi and Web3 space:
5.1. Enhanced Security:
Pyth Entropy's strong security guarantees can significantly enhance the security of decentralized applications, reducing the risk of manipulation and fraud. The solution uses a decentralized network of data providers and a verifiable delay function (VDF) to generate secure random numbers[9].
This approach makes it extremely difficult for any single entity to predict or manipulate the outcome, thereby increasing the overall security of applications relying on randomness.
5.2. Improved UX (User Experience):
By providing fast and reliable randomness, Pyth Entropy can improve the user experience in applications such as blockchain gaming and NFT mints, where quick and fair outcomes are essential. Entropy also guarantees reliable, responsive callbacks to keep your app running[12].
5.3. Enabling New Applications:
With secure on-chain randomness, new types of fair and transparent on-chain applications become possible. This can drive innovation and expand the range of use cases for blockchain technology.
For instance, complex multi-party games, sophisticated prediction markets, and advanced cryptographic protocols that require unpredictable inputs can now be implemented more effectively on blockchain platforms[12].
5.4. Increased Trust:
By addressing the challenges of on-chain randomness, Entropy can increase trust in blockchain-based random number generation, fostering greater adoption of decentralized applications.
5.5. Cost-Effective Solution:
Pyth Entropy offers a cost-effective solution for obtaining randomness on-chain. Traditional methods of generating randomness on blockchain can be expensive due to the computational resources required. Pyth Entropy's efficient design and use of off-chain computation for the VDF calculation help keep costs low for developers and end-users.
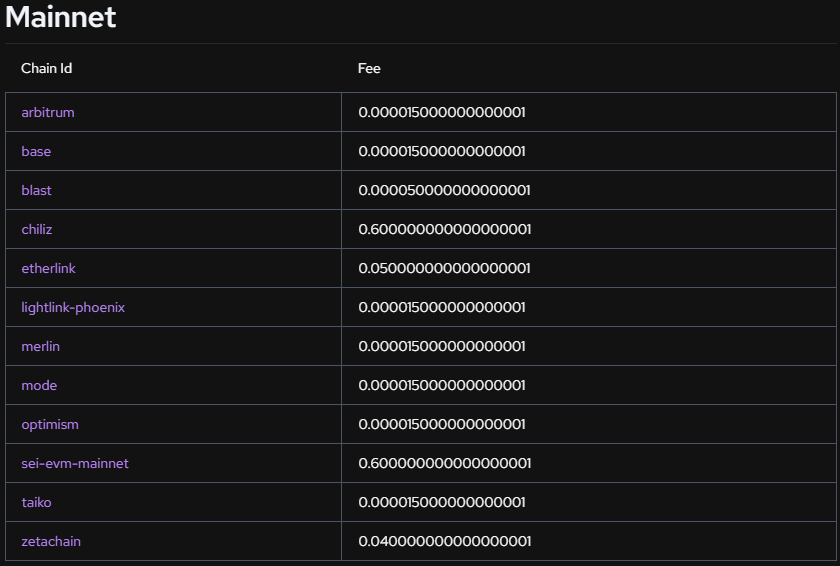
5.6. Cross-Chain Compatibility:
Pyth Entropy is designed to be blockchain-agnostic, with initial support for Solana, and has expanded to other major blockchain platforms. This cross-chain compatibility allows developers to implement consistent randomness across different blockchain ecosystems, facilitating interoperability and expanding the potential user base for applications.
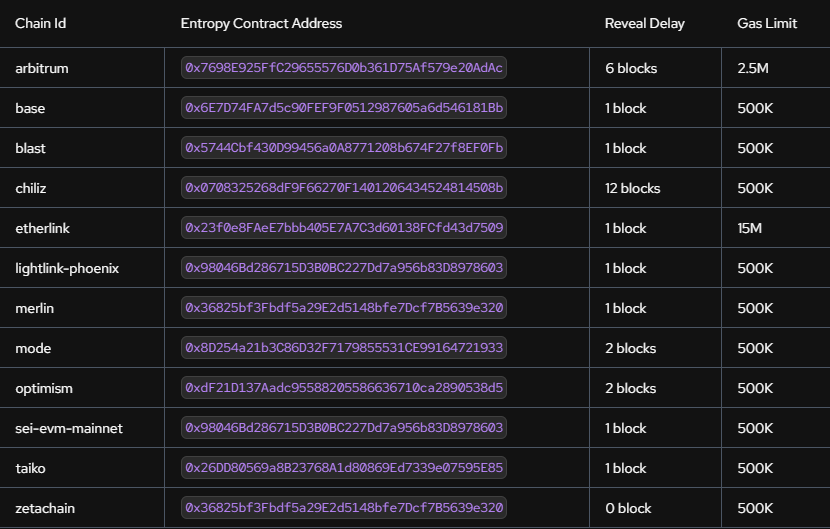
5.7. Regulatory Compliance:
The verifiable and auditable nature of Pyth Entropy's randomness generation process can help applications meet regulatory requirements, particularly in industries like gaming and gambling where provable fairness is crucial. This could potentially open up new markets and use cases for blockchain technology in regulated industrie
6. Real-World Use Cases
Entropy's capabilities open up possibilities for various applications:
Fair NFT Distributions and Reveals:
Randomness is crucial for ensuring fair distribution and reveal of NFTs, preventing manipulation and ensuring a level playing field for all participants.
Secure Random Selection in DAOs and Governance:
Decentralized Autonomous Organizations (DAOs) often require random selection processes for tasks such as committee member selection or voting. Entropy ensures these processes are fair and transparent.
Provably Fair Gambling and Gaming Applications:
Pyth Entropy can ensure that outcomes in gambling and gaming applications are truly random and provably fair, enhancing user trust and regulatory compliance. For example, in a “coin flip game” [16], Pyth Entropy can provide a fair and transparent mechanism to determine the result, assuring players that the game is not rigged
Randomized Task Allocation in Decentralized Computation Networks:
In decentralized computation networks, tasks need to be allocated randomly to prevent collusion and ensure fair distribution of work. Entropy provides a secure solution for this requirement.
7. Challenges and Considerations
While Entropy presents a promising solution, some challenges and considerations remain:
Adoption by Developers. Encouraging developers to adopt and integrate Entropy into their projects is crucial for its success. This requires comprehensive documentation, support, and community engagement.
Scalability Concerns. As the usage of Entropy grows, scalability may become a concern. Ensuring that the system can handle a large number of requests without compromising performance is essential.
Ongoing Security Audits and Monitoring. Continuous security audits and monitoring are necessary to ensure that Entropy remains secure against evolving threats and vulnerabilities.
Regulatory Compliance. Depending on the jurisdiction, regulatory compliance may be a consideration for applications using Entropy. Ensuring that the solution adheres to relevant regulations is important for broader adoption.
8. Conclusion
Pyth Network's Entropy represents a significant step forward in addressing the challenge of secure on-chain randomness. By providing a fast, reliable, and trustworthy source of random numbers, Entropy has the potential to unlock new possibilities in the DeFi and Web3 space. As the solution gains adoption and proves its efficacy, it could play a crucial role in driving innovation and building user trust in decentralized applications.
In summary, the integration of secure randomness through solutions like Entropy is not just a technical enhancement; it's a foundational requirement for the next wave of decentralized applications. Ensuring fairness, security, and transparency in randomness can lead to more robust, trustworthy, and engaging applications, driving forward the adoption and maturity of the blockchain ecosystem.
References:
[1] https://ethereum.stackexchange.com/questions/83847/what-is-meant-by-on-chain-randomness-what-is-the-difference-between-on-chain-an
[2] https://chain.link/education-hub/randomness-web3
[3] https://bitcoin.stackexchange.com/questions/1863/why-was-the-target-block-time-chosen-to-be-10-minutes
[4] https://ethereum.stackexchange.com/questions/149349/why-are-ethereum-slots-12-seconds
[5] https://pyth.network/blog/pyth-entropy-random-number-generation-for-blockchain-apps
[6] https://docs.pyth.network/price-feeds/pull-updates
[7] https://docs.pyth.network/entropy/best-practices
[8] https://docs.pyth.network/entropy/contract-addresses
[9] https://crypto.stanford.edu/~dabo/pubs/papers/VDFsurvey.pdf
[10] https://en.wikipedia.org/wiki/Entropy
[11] https://docs.pyth.network/entropy/protocol-design
[12] https://pyth.network/entropy
[13] Talk by Ben Fisch at BPASE 18, Stanford Cyber Initiative
[14] https://docs.pyth.network/entropy/current-fees
[15] https://docs.pyth.network/entropy/contract-addresses
[16] https://docs.pyth.network/entropy/examples
Feel free to reach out to me on Twitter @Oxmarkdams with any suggestions or opinions (I value genuine feedback or critique). If you find this even slightly insightful, please share it — I’ve invested “countless hours” of refining this content, and your support means everything in helping it educate a wider audience. Thank you.